Cybersecurity Seniors Attend NEDSI Conference and Present Research Topics

A group of Cybersecurity Management seniors from the 2024 Fall Semester capstone class traveled to Hershey, PA, for the 54th annual NEDSI conference, where they presented their research topics for judging.
In the 2024 Fall Semester, Dr. Tamara Schwartz, D.B.A., Associate Professor of Cybersecurity and Strategy, held the CYB 490 Cyber Senior Seminar course for the senior Cybersecurity Management majors of York College of Pennsylvania. There, they researched topics that interested them within their major, ranging from gaming platforms to medical technology, and then wrote a research paper about what they discovered.
“The goal of this capstone class is to empower students to explore how technology, data, and cybersecurity are reshaping the industry of their choice,” Dr. Schwartz said. “Designed to prepare students for real-world challenges, the class fosters subject matter expertise, cultivates continuous learning habits, and strengthens research and analytical skills. At its core, the course challenges students to break down complex, rapidly evolving scenarios into focused, actionable questions and pursue answers amid uncertainty and constant change.”
However, the end of the semester wouldn’t be the end of their research topics. In March 2025, Dr. Schwartz escorted several of her cybersecurity seniors (plus one recent alumnus) to the 54th annual Northeast Decision Sciences Institute (NEDSI) conference, where they had the opportunity to not only network with the other students and professionals at the event but also do poster presentations on their research.
The 54th Annual NEDSI Conference
The NEDSI Conference is a regional meeting held each year, giving graduate and undergraduate students the opportunity to showcase their research, network with other professionals within their field, and attend sessions and workshops about different topics related to cybersecurity.
This year, the conference’s theme was “Generative AI to Enhance Supply Chain Resilience,” and took place March 27th-29th, 2025.
The York College students took a day trip to Hershey, PA, to attend the conference on Friday, March 28th. On that day, the conference held two poster presentation sessions during which students displayed their research and held discussions with anyone who came by and expressed interest. At the end of the day, awards were given to the top research papers and presentations.
“[The NEDSI conference] exposed [the seniors] to cutting-edge ideas, connected them with professionals in their field, and helped them understand how their work fits into a broader academic and professional landscape,” Dr. Schwartz said. “The experience strengthened their communication skills, boosted their confidence, and allowed them to engage with a vibrant community of peers and experts. Most importantly, it added meaningful credentials to their resumes through the presentation of published, award-winning research.”
Conner Everett - Assessing the Security of Operational Technology Industrial Control Systems Controlled by Information Technology Assets
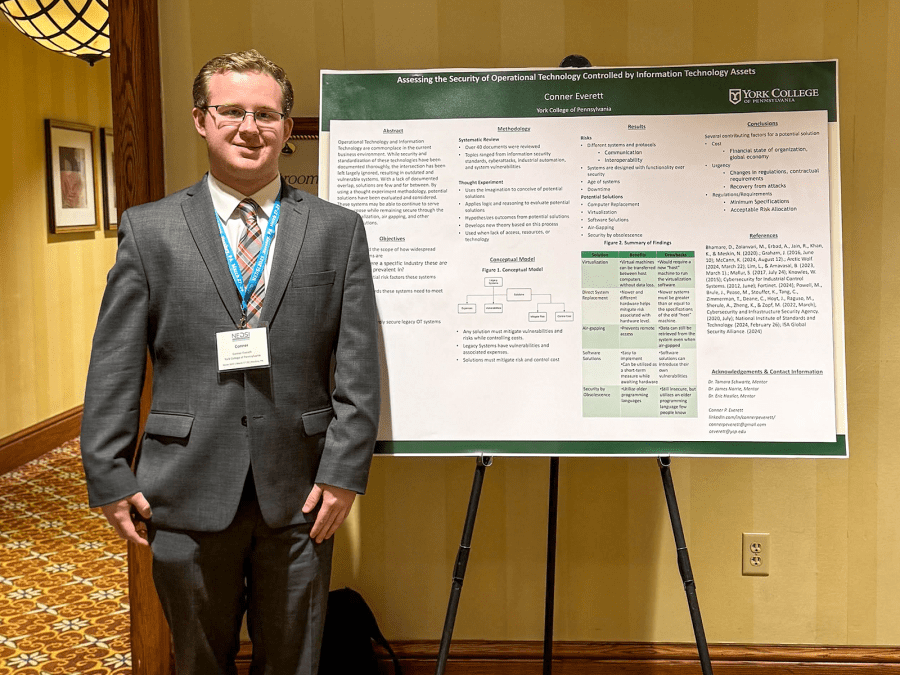
When Conner Everett ‘25, a Cybersecurity Management major with a Business Analytics minor, was working at different technology companies, he couldn’t help but notice that some of them had operating systems hooked up to older Windows models, such as Windows XP or 95. Conner was unsure whether using older models would be safe for the companies’ networks, but learned from their IT teams how they did it.
Four years later, Conner decided to delve further into the topic, taking a closer look at how computers using older operating systems can still control industrial machinery and be secured.
“[I wanted] to see, ‘Okay, these systems aren’t supported anymore, but they’re used in critical infrastructure and manufacturing. What are some methods in which we can use to secure them, and how widespread of a problem is this?’” Conner said. “How can we keep the machine alive while also trying to secure the system?”
This isn’t the first time Conner has presented his research topic for judging. He also attended the Military Operations Research Society (MORS) Conference in Alexandria, Virginia on December 4th, 2024.
Nevin Ferry - High Scores, Dark Agendas: Radicalization Within Gaming Platforms
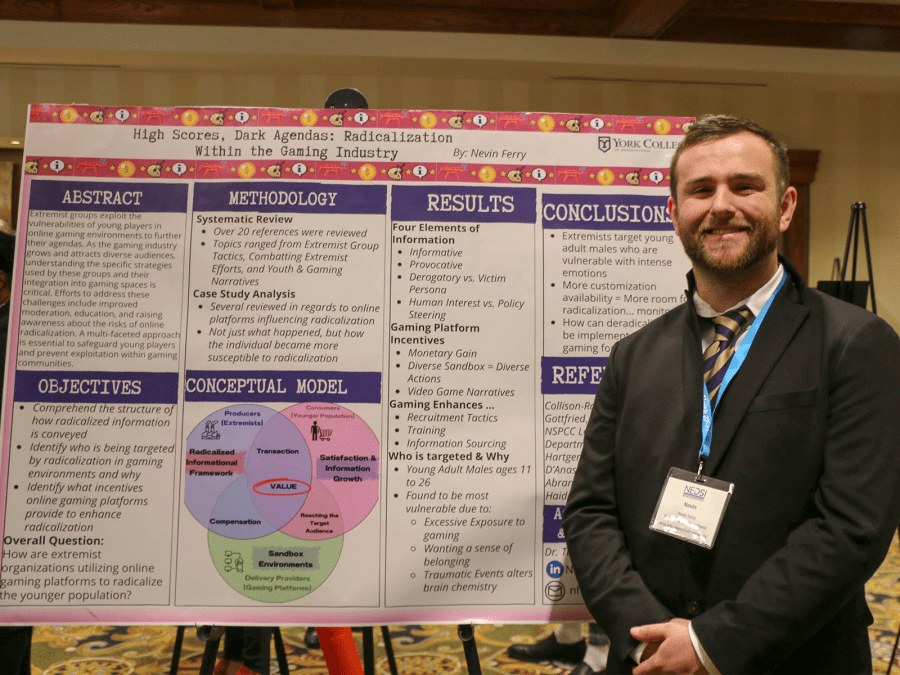
Since he was young, Nevin Ferry ‘25, a Cybersecurity Management major, has loved video games. As he was considering topics, Nevin found himself gravitating towards this long-held interest and unveiled a growing issue within the younger gaming generations: radicalization within gaming platforms such as Minecraft and Roblox.
“[My topic] is more or less about how extremist organizations are utilizing video game platforms to radicalize individuals,” Nevin said. “Essentially, what that means is how groups with strong agendas are using the video games to reach younger audiences that are more susceptible to radicalization.”
Nevin focused on three main objectives: understanding how radicalized information is conveyed, identifying the people and gaming environments the information is targeting and why, and determining what incentives the online gaming platforms provide to encourage radicalization.
He created a conceptual business model that showed how the radicalization happens, with there being a producer (the extremist organizations), a delivery provider that carries the goods/ideas (the gaming platforms), and consumers (the younger population) who receive them. His research revealed how the information could be distributed and the specific groups it targets.
“Extremists target young adult males who are most vulnerable with intense emotions,” Nevin said, “and because of this radicalization that’s happening underneath of us, with the fact that online gaming environments are coming out with all these new tools to create new things, it’s creating more room for radicalization. So, we need to focus on more initiatives to monitor that.”
Nevin also explored ways in which deradicalization can happen. While current methods exist, such as more online monitoring and creating programs dedicated to deradicalization, they may not always be effective. With time, he is hopeful that more solutions will be available.
“My main focus on this whole research is the fact that there are so many different tools out there, but they’re not acting together, they’re more acting alone,” Nevin said. “So, essentially, how can we either A) improve these tactics that are already going so that they can work better with each other, or B) what new approaches can we start looking at?”
Ian Burns - Patient Privacy: An Ethical Analysis of Emerging Tech in Hospitals
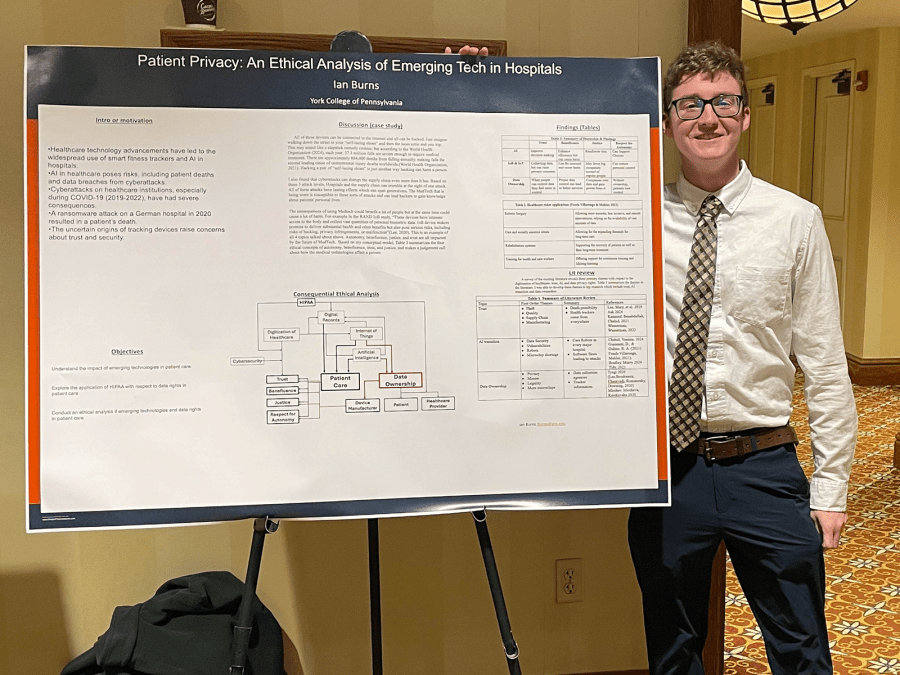
While many of the other seniors in his class chose cybersecurity issues focused mainly on careers in technology, Ian Burns ‘25, a Cybersecurity Management major with a Business Analytics minor, decided to do a topic related to the medical field.
Ian underwent surgery at age four. Now in his early twenties, he wondered how private that information was and how easily the government could access it.
“The main ethics problem that you got to decide between is whether you want to remain private or your will to live,” Ian said. “I found out that there’s location software on pacemakers, diabetes software, everything that will help a person live a normal life, and that data can be subpoenaed if they’re suspected of a criminal case.”
Ian found that there may be situations where the government might subpoena a person’s health data for a situation such as a criminal trial. While there may be good intentions behind the act, it can be seen as a violation of patient privacy. Some situations don’t have good intentions behind them, and the data can be weaponized against a person for a variety of reasons.
“I found out that there’s only two people that should have access to that data: yourself and the hospital,” Ian said. “A tech company or the government should not have access to it because it might impose issues such as with an insurance company. You don’t want it to be sold to a tech company because that’s how the tech company gains data. That data can be sold to an insurance company, and your rates could go up, even if it was something that you had when you were 4 and you’re 22 now.”
Along with these discoveries, Ian found in his research that wearable technology is likely to be everywhere within the next 10-20 years. Soon enough, that technology will expand beyond being worn simply on one’s wrist, chest, and arm; we may find ourselves in a future with tools such as internet-connected glasses, clothes with electric sensors, and headphones that can mitigate headaches. And once they enter the market, health privacy might be harder to come by.
Reflecting on the Experience
By the end of the day, the cybersecurity seniors left the conference in high spirits, having been exposed to various topics and research. Nevin Ferry even won third place overall in the best poster awards, and Devon Tolbert, a graduate of York College, won second place.
“The variety of topics was interesting to me,” Conner said, “We had different topics that we went with, but we also ended up seeing more topics there too. Like, there were people who were [doing] IT stuff with phishing, then there were also people with athletics research too, and how it relates to AI.”
The conference opened the students’ eyes to the future of cybersecurity and technology within the next few decades. There is so much to be excited about, but at the same time, it reminded them that cybersecurity isn’t just about the machinery and products being produced and upgraded, but about how they will affect and protect the people using them.
“One of the big things with cybersecurity is a lot of people are focused more on the technology side of things,” Nevin said, “but one of the big components of cybersecurity itself that I’ve learned through the program here is that it's not just about technology, but the people.”
As they prepare for their incoming May 2025 graduation, the seniors expressed how grateful they were for the experiences they had and the support they received over the past four years. Their professors played a pivotal role in encouraging the students to pursue their interests and reach their goals, and now that they are getting ready for the next chapters of their lives, they look back and see the impact their professors and advisors had on them.
“Talk to Dr. Schwartz, [and] talk to Dr. Norrie; they have a lot of knowledge that they are willing to share,” Conner said. “Just take whatever opportunities you can because your time in college will go fast, and you want to get as much out of it as you possibly can.”
“Don’t just focus on one topic [or] area of learning,” Nevin said. “There are so many different aspects of cybersecurity to learn out there, and you just don’t know exactly who, per se, or what has that information that could also help with another issue.”
“Keep your head on straight,” Ian said. “It’s a whirlwind, [so] it’s easy to get overwhelmed. It’s a process. If you stick with it and you’re actually determined to get through it, you’ll get through it.”